In today’s installment:
- dmesg from before the machine crashed
- Kill process ID from pidfile
- Let systemd retry a task
- Set MTU on OpenVPN connections in Networkmanager
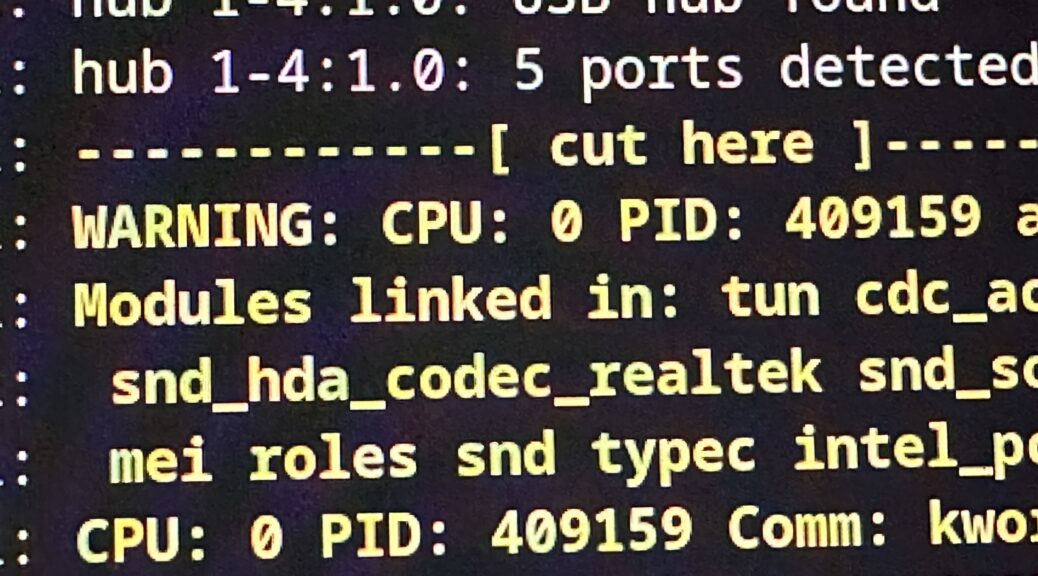
dmesg from before the machine crashed
Super helpful and complete after most kernel panics and Magic SysRq resets:
journalctl --dmesg --boot -1
Kill process ID from pidfile
pkill --pidfile foo.pid
I use this in this wacky systemd user unit:
[Unit]
Description=nginx restreamer
[Service]
ExecStart=/usr/sbin/nginx \
-c %h/.local/nginx/nginx.conf \
-g "pid %h/.local/nginx/nginx.pid;"
ExecReload=pkill -HUP --pidfile %h/.local/nginx/nginx.pid
[Install]
WantedBy=default.target
Let systemd retry a task
Not the first appearance of systemd-run in this category, and probably not the last. Here’s how to hand a task to systemd-run in order to be retried a number of times.
My bro math for interval calculation goes like this:
- RestartSec = Time to wait between end of a failed attempt and start of the next attempt
- RuntimeMaxSec = Allowed time for each attempt
- StartLimitBurst = Number of attempts to make
- StartLimitIntervalSec = (RestartSec + RuntimeMaxSec) x StartLimitBurst x 10
So for a service that shall retry every 5 minutes (RestartSec), 12 times (StartLimitBurst), and shall be timed out after 30 seconds (RuntimeMaxSec):
systemd-run \
--user \
--property=Restart=on-failure\
--property=RestartSec=300 \
--property=RuntimeMaxSec=30
--property=StartLimitBurst=12 \
--property=StartLimitIntervalSec=39600 \
sh -c 'test -e /tmp/1 && touch /tmp/1'
Set MTU on OpenVPN connections in Networkmanager
Is this really still required?
sudo install -m 0755 /dev/stdin /etc/NetworkManager/dispatcher.d/vpn-up << "Here"
#!/bin/sh
if [ "$2" = "vpn-up" ]; then
ip link set dev "$1" mtu 1392
fi
Here